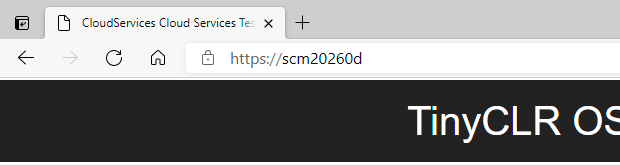
no certificate error (scm20260d is the result of implemented NetBIOS name resolution)
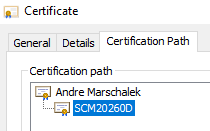
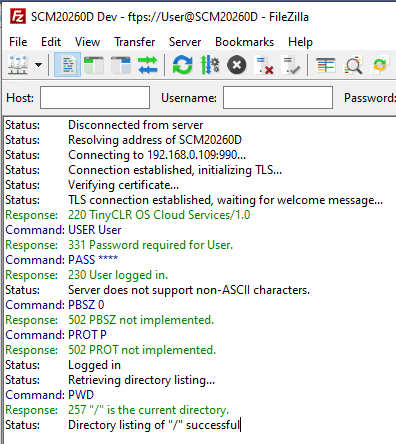
not only HTTPS, also FTP over TLS
(TinyCLR OS v2.1.0-preview4)

no certificate error (scm20260d is the result of implemented NetBIOS name resolution)

not only HTTPS, also FTP over TLS

(TinyCLR OS v2.1.0-preview4)
@Austrian_Dude - was that a self-signed cert? Would you be willing to share how you created it? “How to create usable server certs” would be a great addition to the docs.
This is impressive and I want it… Can I send you some beer? 
yes, self signed
i am doing it with Linux, meanwhile easy with WSL (Windows Subsystem for Linux) on Windows 10
that’s what i thought too, the docs should be extended
happy to share my way -> github ghi docs
yes you can
PayPal.Me
![]()
Oida do gibts no an Österreicha. Servas! (For all non austrian: Dont try to translate this with google translate) 
Nice work. I hate to work with certificates. There are always new reasons why something doesn’t work
Die Welt ist immer wieder kleiner als man glaubt  Servas!
Servas!
Nach Jahren Abstinenz wieder retour …
me, too…
new obscure and inscrutable reasons
…the antidote is documentation
Your work here is fantastic!
For what it is worth… Here is a simple PowerShell script that uses OpenSSL compiled for windows to create a self- singed cert that works great for TinyCLR.
steps how to create certificates …
download openssl from
https://slproweb.com/products/Win32OpenSSL.html
install on your pc
suppose my domain names (for my pc/seerver) for this certificates are
so for this reason we need to create file domains.ext with content as below:
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = scm20260d
DNS.2 = 192.168.2.5
open cmd as admin and go to the openssl bin folder
start to generate CA - Certificate Authority certificate
openssl req -x509 -nodes -new -sha256 -days 1024 -newkey rsa:2048 -keyout CA.key -out CA.pem -subj "/C=US/CN=scm20260d"
step 2 convert pem to crt
openssl x509 -outform pem -in CA.pem -out CA.crt
step3 create client private key and do request
openssl req -new -nodes -newkey rsa:2048 -keyout client.key -out client.csr -subj "/C=US/CN=scm20260d"
step 4 create client certificate
openssl x509 -req -sha256 -days 1024 -in client.csr -CA CA.pem -CAkey CA.key -CAcreateserial -extfile domains.ext -out client.crt
Generated results are :
CA.key
CA.pem
CA.crt
client.key
client.csr
client.crt