Originally published at: How Secure is Your IoT Device? – GHI Electronics
How Secure is Your IoT Device?
Sadly, most IoT designs utilize one of the available networking modules, like WiFi or mobile modules, and it is assumed that the connection is secure. Well, it’s NOT!
TLS Standard
To secure a connection, we have to consider how data flows from point A to point B. The world today relies on TLS (Transport Layer Security), for everything from simple emails to complex banking. The problem with TLS is that it uses complex cryptography and needs plenty of system resources. Those resources are abundant on PCs, but they are very limited on IoT devices. The need for TLS in IoT applications opened up the market to WiFi and cell modems that have built in TLS support.
Weakest Link
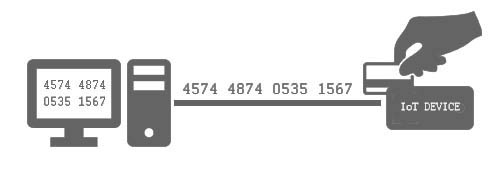
The super secure IoT modules with built in TLS support have a very secure connection between the internet and itself. However, all cryptography happens inside the module and then a simple serial connection is utilized between the module and the IoT device’s main microcontroller to transfer data. This is the raw data, and could be a credit card number! In this example, the weakest link is the serial connection which exposes all data as is.
For illustration, images will show the encrypted data as ####.
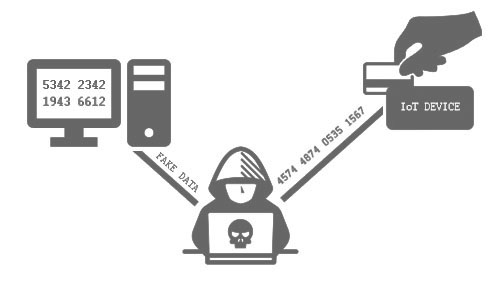
A hacker can very easily add two wires to read all the serial data and even inject fake data.
The Solution
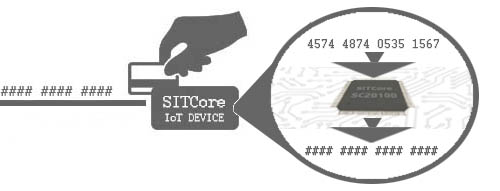
The best way to secure the data is to handle all complex TLS and cryptography internally — inside the microcontroller chip itself. GHI Electronics TinyCLR OS does just that by by implementing TLS right in its core. Unencrypted data never leaves the microcontroller, providing maximum security for your data all the way from the Internet to the inside of your device.

Upping up Security
While you may have a very secure connection from the Internet to the system, it is possible to hack into the system itself. A hacker could potentially scan any external memory chips for raw data. GHI Electronics SITCore products keep the entire system in internal memory. External memory is used only for image buffers and for a special type of optional user buffer.
Nothing is 100% Secure!
It is important to always remember that nothing is 100% secure. Can someone de-cap a chip (open it up) and start probing internal signals? Yes they can, but the cost to do so is prohibitive.